Introduction
In this article, we will see together the fundamentals of Networking on AWS. We will discuss basic components and notions you should know in order to properly start to manage your cloud on AWS.
VPC
Let’s start with VPCs ! A Virtual Private Cloud is basically a private network linked to a specific region which you can use to deploy your resources (i.e EC2 instances.) This virtual network closely resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS. A VPC uses the following components :
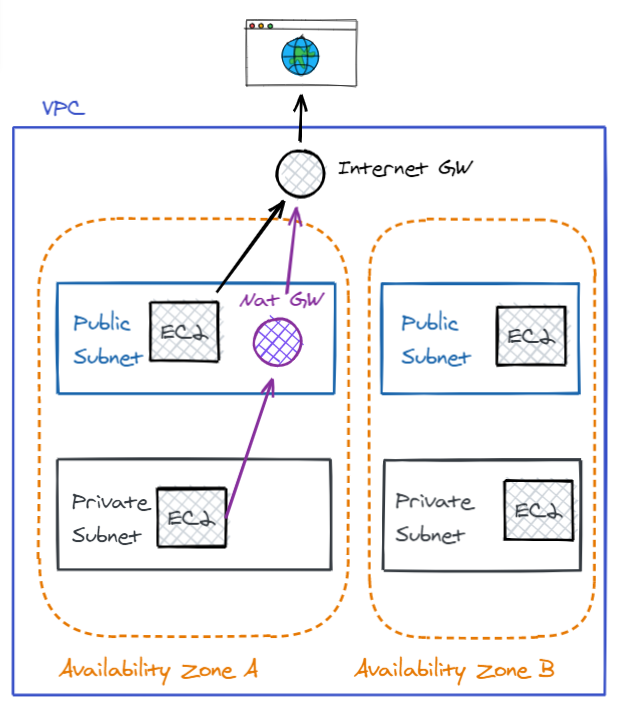
- Subnet — A range of IP addresses in your VPC.
- Route table — A set of rules, called routes, that are used to determine where network traffic is directed.
- Internet gateway — A gateway that you attach to your VPC to enable communication between resources in your VPC and the internet.
- Nat Gateway — enable instances in a private subnet to connect to the internet or other AWS services, but prevent the internet from initiating a connection with those instances.
Here is a summary of what we have just discussed :
Network Security
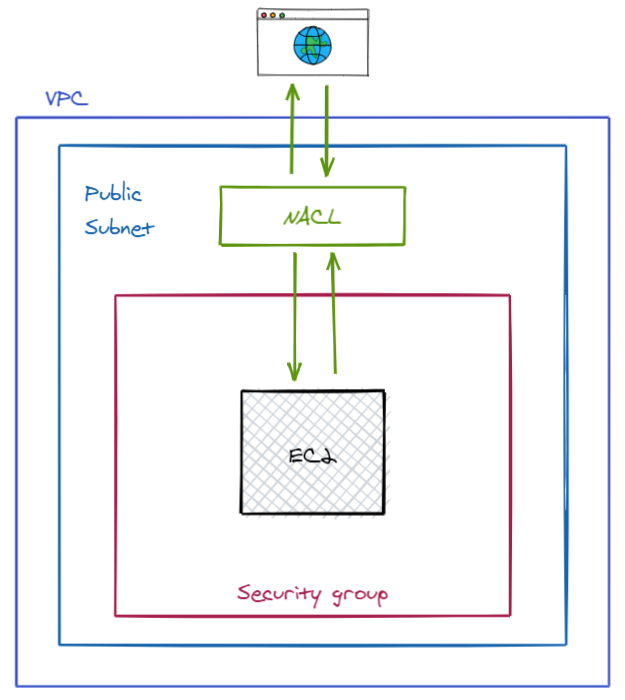
There are basically 2 ways of configuring security in your VPC.
- Security Groups — A security group acts as a virtual firewall for your instance to control inbound and outbound traffic.
- Network Access Control List (NACL) — A NACL is layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
Basically security group is the firewall of EC2 Instances whereas Network ACL is the firewall of the Subnet. Subnet can have only one NACL, whereas Instance can have multiple Security groups.
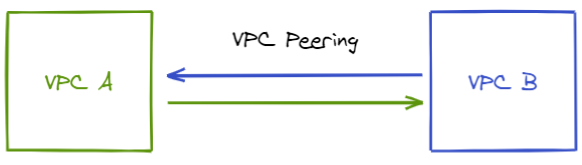
VPC Peering and VPC Endpoints
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network.
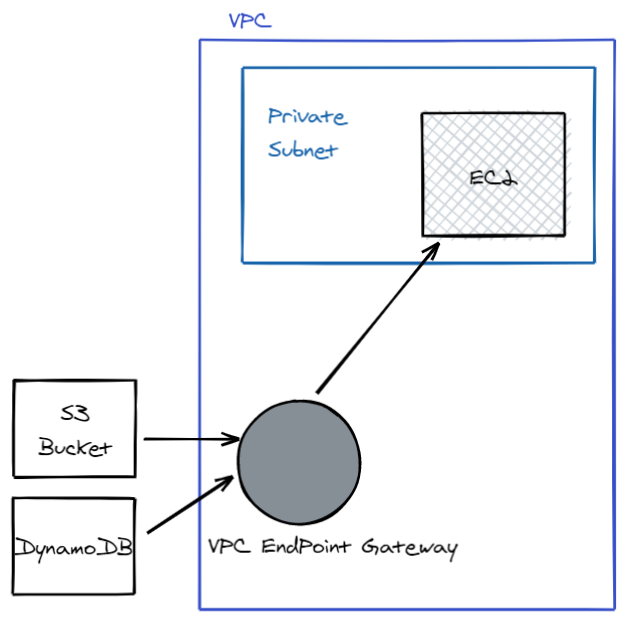
VPC endpoint — Enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection.
Direct Connect and Site to site VPN
If you want to connect your On-Premise datacenter to your VPC, there are two options :
- Site-to-site VPN : it will enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection, and configuring routing to pass traffic through the connection. The connection will be encrypted and goes over the public internet. It can be configured very fast.
- Direct Connect (DX) : Used to establish a physical connection between on-premises and AWS. The connection will be private secure and fast and go over the private network. It is obviously more expensive and will take at least a month to establish it. However it will be more secure than a Site-to-site VPN.
Transit Gateway
Finally, AWS Transit Gateway connects VPCs and on-premises networks through a central hub. This simplifies your network and puts an end to complex peering relationships. It acts as a cloud router – each new connection is only made once.
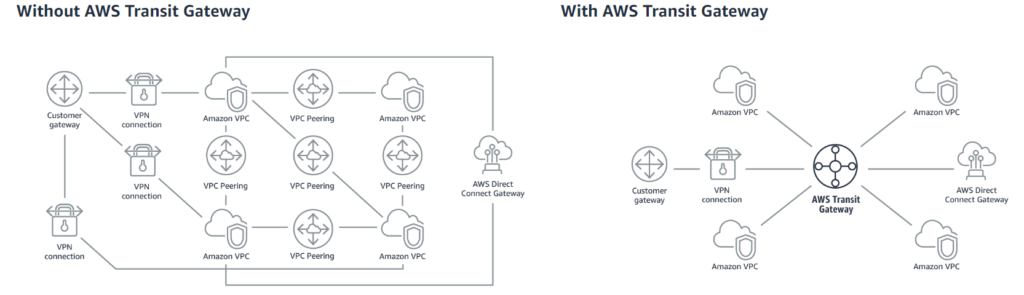
Your network is streamlined and scalable. AWS Transit Gateway routes all traffic to and from each VPC or VPN, and you have one place to manage and monitor it all.
Sources
aws.amazon.com

