Introduction about Configuration Automation and DevOps
Information technology operations and Software development have never worked together as much as today in the workplace. DevOps have now the duty to shorten the delivery, apply fixes and perform updates as fast as they can. They use for that, best practices and methodologies with a sets of tools, known as “toolchains”:
- Coding (code development)
- Building (continuous integration)
- Testing (continuous testing)
- Packaging (staging)
- Releasing (change management)
- Configuring (Infrastructure as Code)
- Monitoring (end user experience)
In this article, we will take a deeper look at “Infrastructure as Code”.
Famous tools like Puppet, Chef, Salt or Ansible bring visibility to configuration of servers and help to automate things. Automation is here to avoid manual mistakes, to be more efficient and productive. But what are the main differences between those four Continuous Configuration Automation tools?
Quick Comparison between Chef – Ansible – Puppet – Salt
I have tried through the help of referred sources, simplify as much as I could, pros and cons for each solution in that tab:
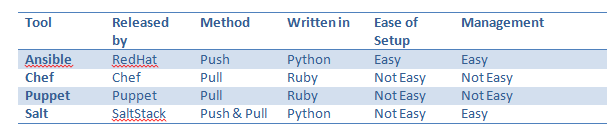
Even if they are all Highly Scalables and Interoperables, the setup and the management are the main pros for Ansible. In my opinion, it’s the best solution with very few cons:
- It increased focus on orchestration over configuration management.
- SSH communication slows down in scaled environments.
- It requires root SSH access and Python interpreter installed on machines, although agents are not required.
Ansible is so easy to use and to setup. As we usually say “keep it simple”!
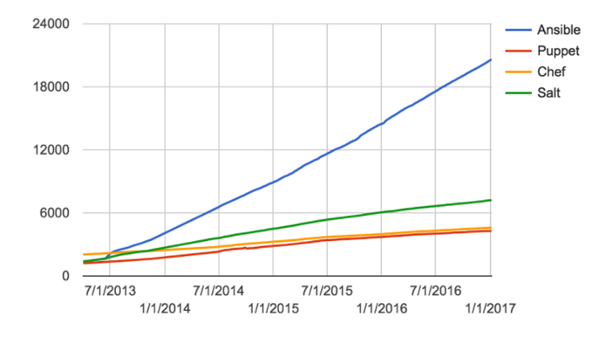
With Salt, Puppet and chef, the installation process is not as smooth as Ansible and documentation is not as good as it should be. Moreover, if we analyze the popularity of these tools, we can see how Ansible is dominating the IT Field in the last years!
How to install Ansible on Centos 7
As I said previously, it’s really easy to install Ansible.
Just run the two following commands on your CentOS server:
yum install epel -y yum install ansible –y
You have now installed Ansible on your server!
In the next example, we will configure 2 LAMP servers with Ansible.
So we have for our example 3 VMs :
- 192.168.10.1 : Centos7 Ansible VM (freshly installed)
- 192.168.10.2 : Centos7 webserver1
- 192.168.10.3 : Centos7 webserver2
Let’s configure our managed servers
First, let’s create the file which will be detected by Ansible for known hosts:
touch /etc/ansible/hosts
We can order VMs in different groups. In that file, we add our servers. In our case 2 webservers in the following group :
vi /etc/ansible/hosts # group web with our 2 webservers
[web]
webserver1 ansible_ssh_host=192.168.10.2 webserver2 ansible_ssh_host=192.168.10.3
Finally, we have to generate ssh keys to let our Ansible VM communicates with webservers:
# ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Created directory '/root/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: d8:de:8e:f9:a4:44:07:a7:ec:dc:ed:81:20:ef:1e:b8 root@rhelsrv1 The key's randomart image is: +--[ RSA 2048]----+ | | | | | o . | | + * | | . S o | | = B o | | * B o | | . O o . | | E.+ . | +-----------------+
We push the public key on our 2 “webservers” (check if needed with a telnet that port 22 is opened for your Ansible VM):
# ssh-copy-id 192.168.10.2 # ssh-copy-id 192.168.10.3
Finally, we can run the following ansible command to check that Ansible can reach both webservers:
# ansible –m ping all
Output
Webserver1 | SUCCESS => {
"changed": false,
"ping": "pong"
}
Webserver2 | SUCCESS => {
"changed": false,
"ping": "pong"
}
Ansible, Modules, YAML and Playbooks
As explained at the beginning of this article, our goal is to automate things. So we can’t use the Ansible command line forever. We will use Playbooks and modules.
Playbooks are Ansible’s configuration, deployment, and orchestration language. They can describe a policy you want your remote systems to enforce, or a set of steps in a general IT process. Ansible ships with a number of modules (called the ‘module library’). These modules can control system resources, like services, packages, or files (anything really), or handle executing system commands. If Ansible modules are the tools in your workshop, playbooks are your instruction manuals, and your inventory of hosts are your raw material. The Ansible documentation is so great !
You can find playbook examples here: https://github.com/ansible/ansible-examples
As you can see, Playbooks are written in YAML. YAML is a data-orientated human readable serialization language, and I have come across it in many projects including OpenAPI, Docker, Kubernetes and Ansible playbooks among others.
It is so easy to learn! You can read the great following article if you are interested in learning YAML in 5 minutes : https://www.codeproject.com/Articles/1214409/Learn-YAML-in-five-minutes
And Check how many modules are availables : https://docs.ansible.com/ansible/latest/modules/list_of_all_modules.html
Let’s configure our LAMP servers using a Playbook
In this example, we will configure our webservers using the following yaml playbook :
# vi lamp.yml
---
- hosts: webservers
handlers:
- name: restart httpd
service: name=httpd state=restarted
tasks:
- name: 1. Apache Installation
yum: name=httpd state=present
- name: 2. PHP Installation
yum: name=php state=present
- name: 3. Install PHP Extensions
yum: name={{item}} state=present
with_items:
- php-pdo
- php-mysql
- php-soap
- php-gd
- php-pear-MDB2-Driver-mysqli
- name: 4. MariaDB Installation
yum: name=mariadb-server
- name: 5. Starting Apache
service: name=httpd state=running enabled=yes
- name: 6. Staring MariaDB
service: name=mariadb state=running enabled=yes
- name: 7. Index Installation
copy: src=lamp.yml.index.php dest=/var/www/html/index.php
notify:
- restart httpd
- name: 8. Firewall configuration
action: command /usr/bin/firewall-cmd --permanent --add-port=80/tcp
- name: 9. Restarting Firewall
service: name=firewalld state=restarted
...
Let’s run our playbook :
# ansible-playbook lamp.yml PLAY [webserver] ******************************************************************* GATHERING FACTS *************************************************************** ok: [webserver1] ok: [webserver2] TASK: [1. Apache Installation] ************************************************ changed: [webserver1] changed: [webserver2] TASK: [2. PHP Installation] *************************************************** changed: [webserver1] changed: [webserver2] TASK: [3. Install PHP Extensions] **************************************** changed: [webserver1] => (item=php-pdo,php-mysql,php-soap,php-gd,php-pear-MDB2-Driver-mysqli) changed: [webserver2] => (item=php-pdo,php-mysql,php-soap,php-gd,php-pear-MDB2-Driver-mysqli) TASK: [4. MariaDB Installation] ******************************************** changed: [webserver1] changed: [webserver2] TASK: [5. Starting Apache] *************************************************** changed: [webserver1] changed: [webserver2] TASK: [6. Starting MariaDB] ************************************************** changed: [webserver1] changed: [webserver2] TASK: [7. Index Installation] ************************************************* changed: [webserver1] changed: [webserver2] TASK: [8. Firewall Configuration] ************************************** changed: [webserver2] changed: [webserver1] TASK: [9. Restarting Firewall] ********************************************* changed: [webserver2] changed: [webserver1] NOTIFIED: [restart httpd] ***************************************************** changed: [webserver2] changed: [webserver1] PLAY RECAP ******************************************************************** webserver1 : ok=11 changed=10 unreachable=0 failed=0 webserver2 : ok=11 changed=10 unreachable=0 failed=0
It’s done !
You have successfully installed 2 LAMP servers using Ansible !

Sources:
- https://www.intigua.com/blog/puppet-vs.-chef-vs.-ansible-vs.-saltstack
- https://www.linuxtricks.fr/wiki/ansible-automatiser-la-gestion-de-serveurs#paragraph_installer-lamp-sous-centos
- https://www.edureka.co/blog/chef-vs-puppet-vs-ansible-vs-saltstack/
- https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-ansible-on-centos-7
- https://docs.ansible.com
- https://wikipedia.org

